VM Patching using Ansible Automation Platform
Lab Overview
In this lab exercise, you will focus on updating only the security-related
packages of the provided RHEL systems using the ansible.builtin.dnf module.
This exercise will target all the VMs listed in your existing OpenShift Virtual
Machines dynamic inventory and will be added to the tasks directory in a file
named update_security_packages.yml within your redhatone.vm_management.vm_management
role.
The following steps will guide you in creating the update_security_packages.yml file
and the corresponding Ansible Playbook that will be called within your Patch
VMs Job Template.
|
To ensure the virtual machines can access the required repositories for patch updates, the environment is configured to use the Vault Credentials provide a significant security advantage: credentials are one-way encrypted, meaning they can be used within automation workflows but never exposed in plain text. This ensures sensitive information remains secure while simplifying credential management. This is a key benefit of Ansible Automation Platform that is often overlooked by ansible-core users. |
Create the update_security_packages.yml file.
-
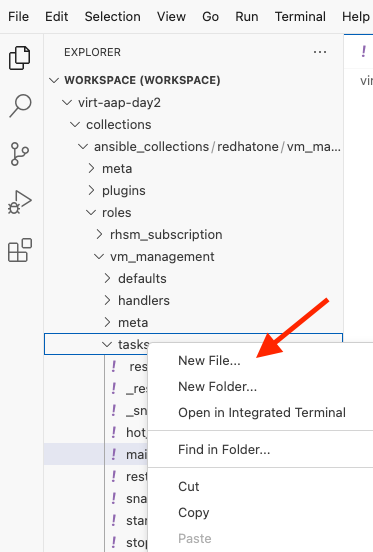
Within your VSCode editor, right click
tasksof thevm_managementcollection and create a New File labeledupdate_security_packages.yml -
Add the following content to the
update_security_packages.yml--- - name: Update security-related packages on all hosts ansible.builtin.dnf: name: "*" security: true state: latest -
Within your
virt-aap-day2directory, create an Ansible Playbook labeledpatch_vm_playbook.ymlwith the following details:--- - name: Patch Virtual Machines hosts: all roles: - redhatone.vm_management.rhsm_subscription - redhatone.vm_management.vm_management -
After making and saving the changes, ensure you commit and push them to your Gitea repository. For detailed instructions, refer to Appendix: Using VS Code or Terminal to Commit and Push Changes.
-
Re-sync the
Workshop Projectwith your latest updates within the Ansible Automation Platform UI-
Navigate to Automation Execution → Projects and select
Workshop Project -
On the top right, select the Sync Project button and wait for
Last job statusto provide the status ofSuccess.
-
Create & Run Update Security Packages Job Template with Ansible Automation Platform
To execute the patch_vm_playbook.yml within Ansible Automation Platform, create a Job Template as follows:
-
Navigate to Automation Execution → Templates, click the Create template button, and choose Create job template.
-
Fill out the following details:
Parameter Value Name
Patch VMs
Job Type
Run
Inventory
OpenShift Virtual Machines
Project
Workshop Project
Playbook
patch_vm_playbook.ymlExecution Environment
Day2 EE
Credentials
Workshop Credential, Vault Credential
Extra variables
task_file: update_security_packages.ymlEnabled Options
Privilege Escalation
-
Click Create job template.
-
Once the Patch VMs Job Template is created, select the Launch Template button on the top right corner to run the job.
-
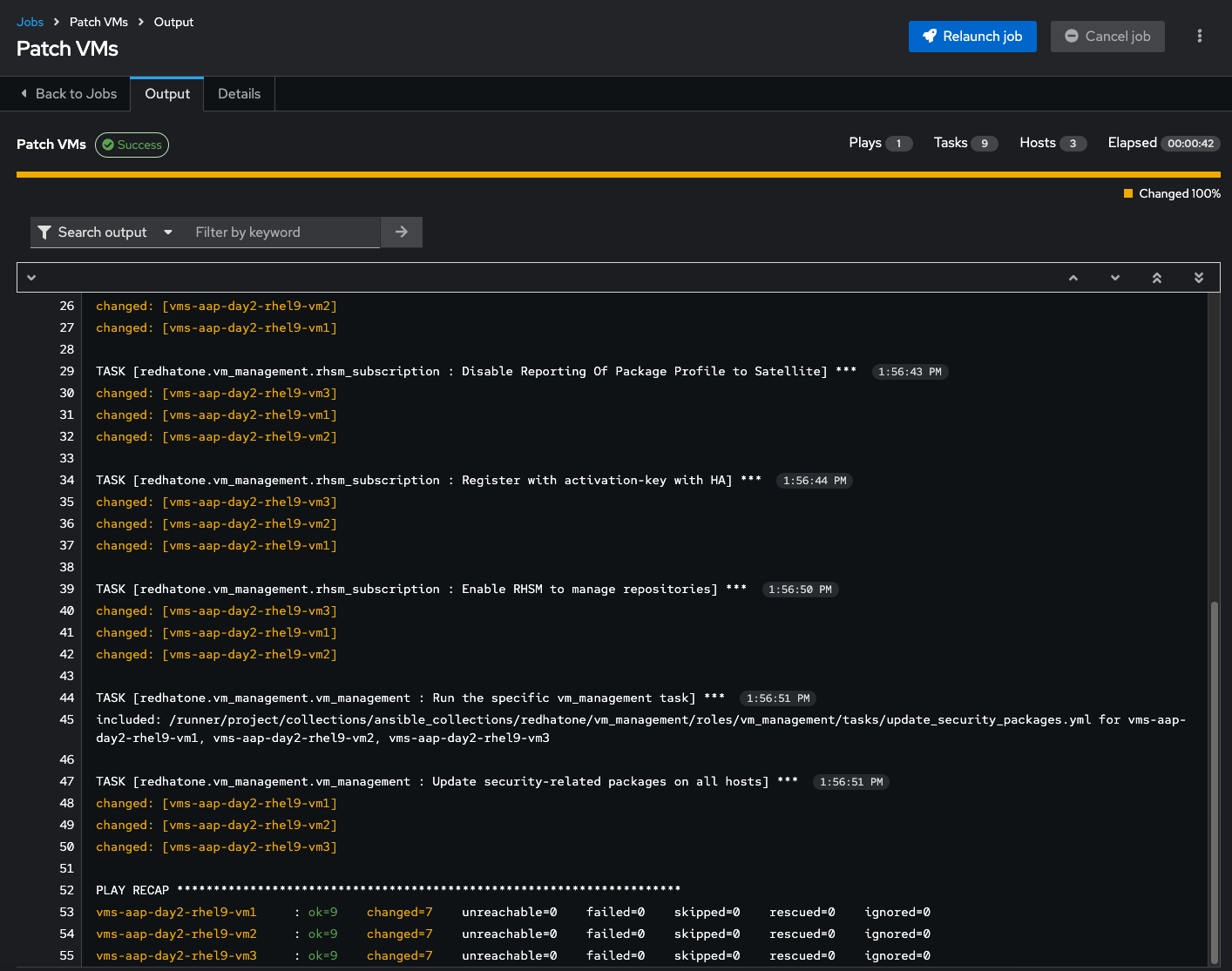
Once the Patch VMs Job is complete, you should see output similar to:
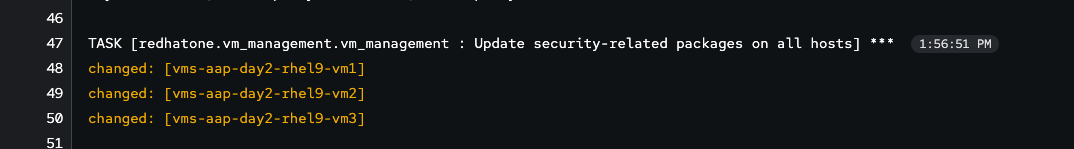
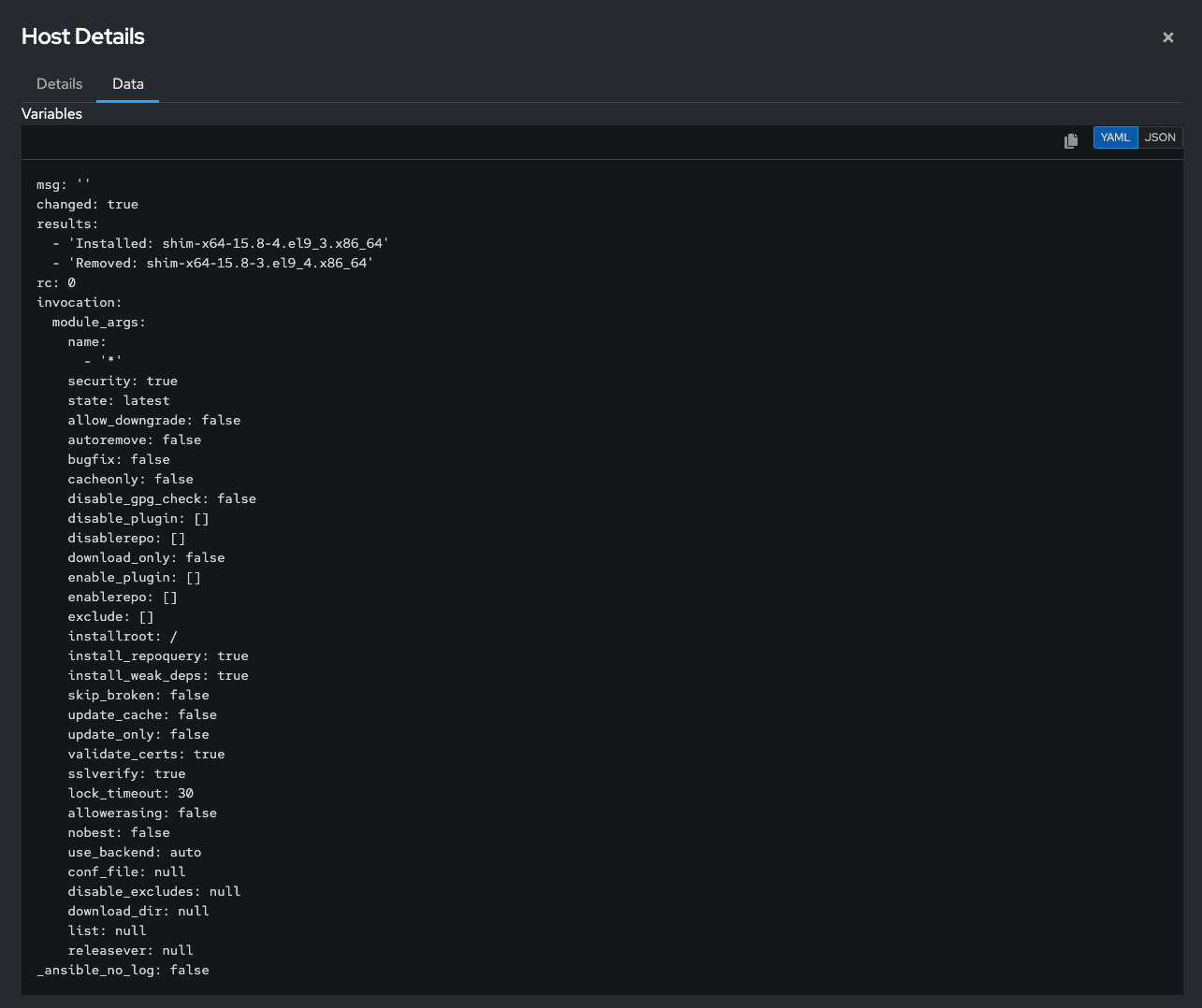
This gives a breakdown of all the tasks that ran and a play recap of the changes made to the different hosts. If you take a closer look at the
Update security-related packages on all hoststask, you can drill into specific host details on what was installed on the system(s).
Conclusion
Well done completing the lab!
You’ve now learned how to automate the patching of security-related packages on
RHEL systems using Ansible Automation Platform. By creating and integrating the
update_security_packages.yml task file and patch_vm_playbook.yml, you gained
practical experience in targeting OpenShift virtual machines for security
updates.
You should now have a clear understanding of:
-
Creating and managing Ansible roles to automate security updates.
-
Developing a playbook to execute tasks using a modular role structure.
-
Synchronizing updates with Gitea and integrating them into Ansible Automation Platform.
-
Automating the patching process through a Job Template.
These skills provide a foundation for maintaining secure and consistent infrastructure at scale. Great job, and continue exploring automation to enhance operational efficiency!